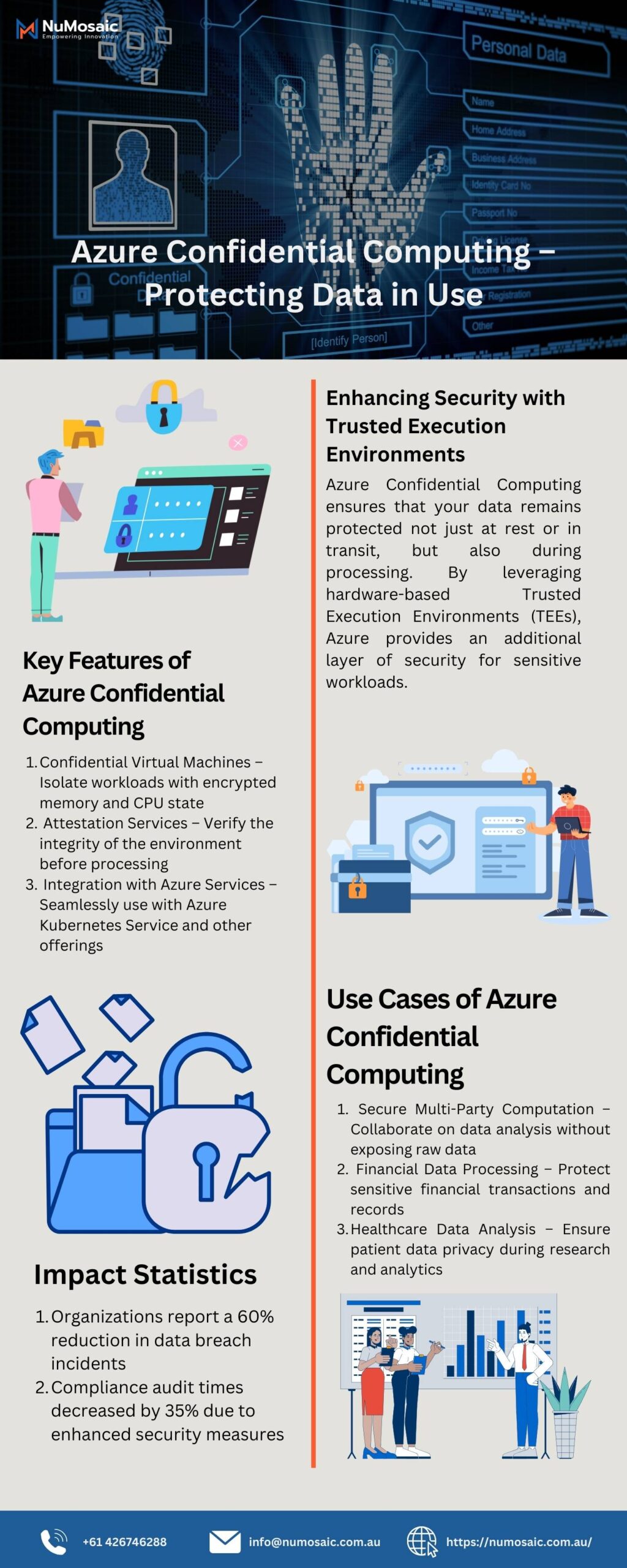
What Is Azure Confidential Computing?
Azure Confidential Computing is a breakthrough cloud security model that protects data in use by running workloads inside hardware-based, isolated environments called Trusted Execution Environments (TEEs) or enclaves.
Unlike traditional security methods that protect data at rest and in transit, this approach secures data during active computation, providing unmatched privacy for sensitive applications.
🛡️ Imagine a secure vault around your app’s memory—while it’s running in the cloud.
Why Confidential Computing Matters
In today’s data-driven economy, privacy and trust are essential. Azure Confidential Computing is ideal for:
🏦 Finance – Secure multi-party computation (MPC), fraud detection, confidential ML
🏥 Healthcare – HIPAA-compliant data processing, genomic analysis
🧑⚖️ Legal & Government – Secure data sharing, protected decision-making
🤖 AI & ML – Protect models and data during inference or training
How It Works
Azure leverages specialized hardware (like Intel® SGX and AMD SEV-SNP) to create hardware-enforced isolation for virtual machines, containers, or app enclaves. Even Microsoft or cloud administrators can’t view the data inside.
Key Components:
Confidential VMs – Run entire workloads in encrypted memory environments.
Confidential Containers – Containerized apps that operate within TEEs.
Microsoft Open Enclave SDK – Build custom confidential applications with full control.
Benefits of Azure Confidential Computing
| Benefit | What It Means |
|---|---|
| End-to-End Data Protection | Data remains encrypted even during processing |
| Zero Trust Architecture | Isolation from other workloads—even admins |
| Compliance-Ready | Meet strict regulatory and industry standards |
| Secure Collaboration | Enable joint computation across untrusted parties |
Real-World Use Cases
Confidential Machine Learning – Train or infer without exposing IP or customer data.
Secure Blockchain Applications – Add privacy layers to decentralized networks.
Joint Research & Analytics – Share sensitive datasets across companies or jurisdictions.
Digital Rights Management – Protect code and assets from tampering or leakage.
💡 Related Read: [Open Source AI Models – Enterprise-Ready and Customizable] (← insert internal link)
Getting Started with Azure Confidential Computing
✅ Choose a supported VM (e.g., DCsv3, DCasv5, ECasv5).
🔐 Enable TEEs or run your code inside a confidential container.
🧪 Use tools like the Open Enclave SDK for full control over enclave development.
Azure also offers pre-built confidential services, like confidential Kubernetes nodes or SQL Always Encrypted with secure enclaves.
Build Securely, Collaborate Freely
With Azure Confidential Computing, you no longer have to choose between cloud scalability and data privacy. It empowers enterprises to build, deploy, and collaborate with confidence—even on the most sensitive data.